In this guide we are going to analyse various attacks that can happen to your cryptocurrency (mostly bitcoin). While it is true that most of the attacks we will talk about are purely hypothetical in nature, we have already seen real life examples of some of the attacks described here (Mt. Gox and Transaction malleability). Before we get started, a huge shout out to the “Game theory and Network attacks” video by “Blockchain at Berkley” for providing the inspiration for the article.
Hypothetical Attacks on Cryptocurrencies
Note: We will be using these two terms a lot in the article below so let’s define it right now:
- Orphan blocks aka orphans: Blocks that couldn’t get added to the main chain despite being successfully mined.
- Hashrate: Basically means how powerful that miner’s computational resources are.
So without any further ado, let’s get started.
What are mining pools?
Before we get into the descriptions of various attacks, let’s understand what a mining pool is (in this section we will be talking exclusively wrt BTC). The entire blockchain works because of a network of “miners”. The miners basically “mine” for new blocks in the blockchain by solving complex cryptographical puzzles using their computational power. As a result of this, they get a mining reward which is 12.5 BTC.
Once they successfully mine a block, they gain the power to put in transactions inside the block. That’s basically how transactions happen in all cryptocurrency, a miner puts in the record of the transaction inside the block.
Now remember one thing, there are only a limited number of bitcoins that were created (21 million coins). Satoshi Nakamoto, the creator of bitcoins, envisaged that as more and more miners got in, the rate of bitcoin mining would exponentially increase, so much so that all the available bitcoins could be mined out in a couple of years!
Now, this could be a disaster for bitcoins, because like all economic commodities, the value of bitcoin lies in supply and demand. If the supply of bitcoins suddenly increases, then that would decrease the demand, which would in turn hurt its value. The supply-demand relationship is one of the most critical economic concepts, the following is what the supply-demand graph looks like:
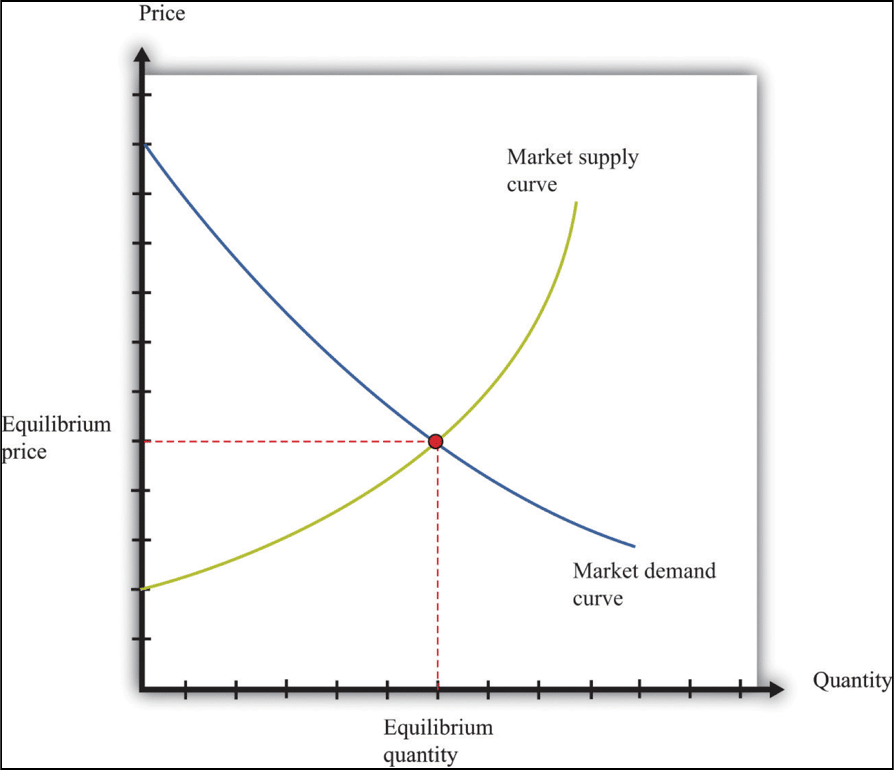
To prevent the supply of bitcoins from going out of hand and to make it a more sustainable model, Satoshi implemented a difficulty adjust system.
What is difficulty adjustment? As more and more blocks get mined, the difficulty of the cryptographic puzzles increase exponentially. Basically, the more bitcoins you mine out, the more difficulty the process of mining becomes. Miners soon found out that they can’t really mine efficiently by themselves anymore, the process was getting more and more expensive. So, they decided to pool their resources together and form cliques and groups to mine bitcoin more efficiently. These groups of miners are called “mining pools”.
Advantages and Disadvantages of mining pools
Advantages
- The pools are run by pool managers. It is far easier to upgrade the overall network because instead of coordinating with random independent miners, the pool managers can simply upgrade the network by themselves.
- Reduces variance in mining rewards:One of the biggest reasons why miners join pools is to reduce variance in their mining rewards. To understand what variance means and how that affects miners, we will need to do some mathematics. Credit to L.M. Goodman and her medium article for the explanation.First, let’s understand what Bernoulli distribution is. The Bernoulli distribution basically states that for every discrete distribution which has two outcomes “success” and “failure” if the probability of success is p (where, 0<p<1), then the probability of failure is 1-p.Now , let’s apply this in bitcoin. If a miner controls a fraction “p” of the overall mining power and as a result, has a probability p of mining a new block where 0<p<1, then, on applying Bernoulli’s distribution, he/she has the probability of (1-p) of NOT mining a new block.In Bernoulli’s distribution: variance = p*(1-p)Now, let’s see how many blocks are mined in a year.Every 10 mins, 1 block is mined. Which means each hour 6 blocks, every day 24 * 6 blocks and every year 365*24*6 blocks are mined.Basically, for a miner who has “p” probability of mining a block, is expected to mine 365*24*6*p blocks per year. That’s their expected return.
Similarly, the overall standard variance that they are going to be facing the entire year is: 365*24*6*p*(1-p).
Now, we shall define “standard deviation”. Standard deviation is a term which defines by how much are the members of a particular distributed group varying from the mean of the group.
In the context of the blockchain and this example, standard deviation is by how much is this miner’s reward going to be deviated from the expected reward.
Standard deviation = [sqrt]variance / expected return.
Now, as we know:
- variance = 365*24*6*p*(1-p)
- expected return = 365*24*6*p
So, on substituting these values we get:
- Standard deviation = [sqrt] (365*24*6*p*(1-p)) / 365*24*6*p
Now let’s take an example. Suppose a miner owns 0.01% of the hash rate in the network. (Meaning p=0.0001).
If you substitute the values accordingly to the standard deviation equation then you will get a standard deviation of 0.4364 OR 43.6%!! A 43.6% deviation from the expected reward or a miner who owns 0.01% hash rate.
The only solution to decrease this deviation and variance is to pool in resources to together to increase the overall hash rate percentage, which is exactly what mining pools offer.
Cons
- A lot depends on the ethics of the pool manager.
- Centralisation:The biggest criticism that most pools face is that they lead to centralization of coins. Let’s see what we mean by that. Checkout the hashrate distribution of bitcoin:
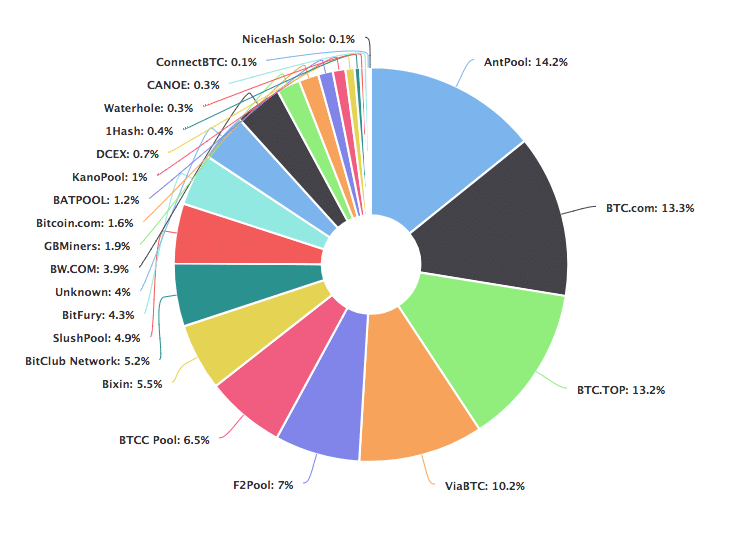 Image courtesy: Blockchain.info~50% of the world’s bitcoin supply is being mined by 4 pools!! Just 4!Bitcoin is supposed to be a decentralized currency, but how decentralized can it really be if nearly half of it is controlled by 4 pools?Unfortunately, this is not a problem exclusive to Bitcoin, checkout the hashrate distribution chart of Monero:
Image courtesy: Blockchain.info~50% of the world’s bitcoin supply is being mined by 4 pools!! Just 4!Bitcoin is supposed to be a decentralized currency, but how decentralized can it really be if nearly half of it is controlled by 4 pools?Unfortunately, this is not a problem exclusive to Bitcoin, checkout the hashrate distribution chart of Monero: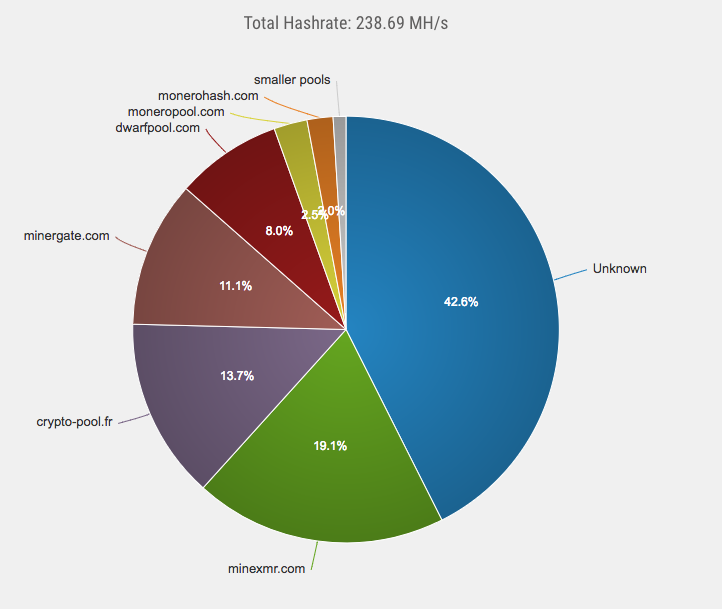
Image Courtesy: Monero Hash.
In Monero 42.6% of the supply is controlled by 1 unknown group!!
When a pool overwhelmingly takes in more and more stake in the hashrate distribution chart, they defeat the purpose of decentralization. We have already seen how important miners are in the context of a blockchain. When a group of miners control so much hashrate, they tend to become the central authority themselves. In fact, when a group of miners take over 51% of the network’s hashrate, they automatically initiate an attack called the “The 51% attack”.
What is the 51% attack?
The 51% attack happens when the 51% of the network’s hashrate is under one entity. That entity could be a mining pool or an authority figure. The moment 51% of the hashrate is under siege, it basically destroys the decentralized nature and opens up the network to a plethora of attacks:
- Selfish mining.
- Cancelling all transactions.
- Double Spending.
- Random forks.
Now, before we go through each of those attacks let’s see how and when can a 51% attack happen.
Case 1: A mining pool becomes too big
The most common form of 51% attacks can happen when a mining pool becomes too big and gets more than 51% hashrate. In fact, this has already happened with bitcoin once before. In July 2014, the popular mining pool GHash.io passed 51% hashrate. They then voluntary cut themselves down and explicitly stated that they would never pass 39.99% hashrate.
In August 2016, Krypton and Shift which are two blockchains based on Ethereum, suffered 51% attacks.
Case 2: Having limitless capital
A powerful entity with limitless capital (like a country or a billionaire) can buy enough equipment to take over the a blockchain. Another interesting variation of this is a “Gold finger attack”.
Picturize this, suppose you are a hostile entity and you have limitless capital at your disposal. You can, in theory, buy all the ASICs and GPUs required to initiate a 51% takeover of the chain. You can then proceed to destroy the value of the coin by either initiating double spends or by bloating up the chain with spam transactions.
Case 3: The proof of work takeover problem
Now this, is a very interesting and diabolical scenario. Vitalik Buterin gave a great example of this by showing how the takeover problem can happen in Ethereum.
Suppose, someone makes a hypothetical smart contract for an activity. The terms of the contract go like this:
- Any miner can join the activity by sending a very large deposit into the contract.
- The miners must send shares of the partially completed blocks that they have mined into the contract and the contract verifies it and also verifies that you are a miner and that you have sufficient hash power.
- Before 60% of the miners in the system join you can leave anytime you want.
- After 60% of the miners join you will be bound to the contract until the 20 blocks have been added to the hardfork chain aka the red chain.
Not only will the new chain grow bigger and longer, since 60% of the entire miners are bound contractually into this new chain this will quickly make the original older chain aka the blue chain irrelevant.
Now, you might be asking why will miners join in a takeover?
Well, let’s see their incentive for joining:
- Possible reward at the end.
- No risk of joining on their part.
What is their incentive to follow through with the contract?
- The huge amount they have deposited in the beginning.
- Once again, the possibility of a great reward.
So, these in nutshell are certain examples of how 51% hashrate can be taken over by one entity. Now, let’s see the repercussions of such an attack.
What are the repercussions of a 51% attack?
As discussed above, the 4 main attacks that can happen directly as a result of the 51% attack are:
- Selfish mining.
- Cancelling transactions.
- Double Spending.
- Random forks.
Selfish Mining
When an entity does manage to get over 51% of the hashing power, the computational advantage that they have over their competitors is truly staggering. Like we have discussed before, miners mine for coins by discovering and adding blocks to the blockchain. The way this happens is that they solve extremely complicated cryptographic puzzles. On discovering the block, the entire network (or at least a majority) needs to acknowledge that it fulfills the necessary proof of work criterion, and then it becomes part of the main chain.
Now, suppose Alice and Bob are two miners. There is a chance that both of them solve the puzzle at the same time for both of their respective blocks. After that, it is all about who the network chooses and agrees to mine on. Eg. If 80% of the network chooses to mine on Alice’s block, then there is a higher chance of them coming up with the next block than the 20% who is siding with Bob (due to the higher hash rate). When this happens, Alice’s block will become part of the chain while Bob’s becomes an orphan block (a block not attached to the main chain).
Now think of this. Suppose Bob has 51% of the hash rate in Bitcoin at his disposal. He can simply mine for blocks and keep mining on top of it without waiting for the network’s approval because he himself represents the majority (since he possesses 51% of the hash rate). So he can simply keep on mining on top of his blocks without bothering to let the network know and collect all the reward and transaction fees.
Cancelling Transactions
How do transactions happen in cryptocurrencies? Long story short, if Alice were to send 1 BTC to Bob, then Alice will have to send the transaction after signing it to the miners, who can then verify and put it in their blocks. That way Bob can then get his 1 BTC. Now if bitcoin were under 51% attack then the chances are that majority of the blocks will be mined by the attacker. In cases like that, it will be entirely feasible for the attacker to not accept any transactions to any of their blocks (which could be all the future blocks in the chain). If this were to happen it will destroy bitcoin.
Double Spending
One of the many important roles that miners have is the prevention of “double spending”. Double spending basically means spending the exact same coin on more than one transactions at the same time. This problem is circumnavigated because of miners. In a blockchain, transactions happen only when miners put the transactions in the blocks that they have mined.
So suppose, Alice were to send 1 bitcoin to Bob and then she sends the same coin to Charlie, the miners would put in one transaction inside the block and, in the process, overwrite the other one, preventing double spending in the process. However, this only works when the miners are not compromised.
In a 51% attack, the miners have already been compromised. As has be stated earlier, in a 51% attack the attacker will most likely be the one adding new blocks to the blockchain. They can then initiate a double spend wherein they can spend the same coin to do more than one transactions.
This attack is generally done to devalue a coin. Like mentioned above, a hostile entity can initiate a “Gold Finger” attack to double spend the coin indiscriminately and destroy its value. Double spending can also happen via “forking”.
Random Forks
So, what is a fork?
A fork is a condition whereby the state of the blockchain diverges into chains where a part of the network has a different perspective on the history of transactions than a different part of the network. That is basically what a fork is, it is a divergence in the perspective of the state of the blockchain.

In the example above the red chain is a fork from the main blue chain.
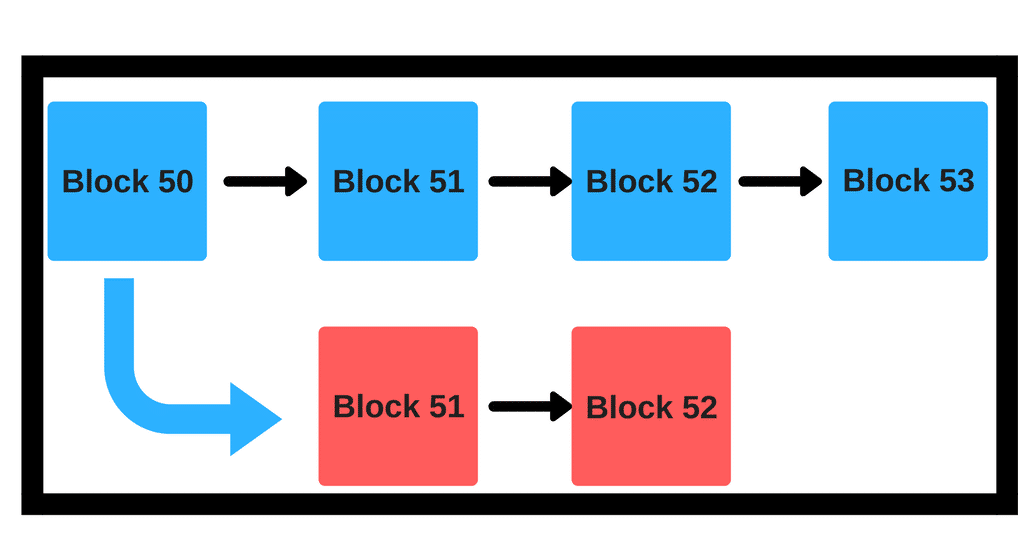
So, why would a currency like bitcoin, under 51% attack, would want to fork from the main chain? Suppose the attacker has spent 20 BTC in block 51 to buy 400 Ethereum (hypothetical scenario). They can then simply do a fork in block 50 to go to block 51. When you fork, you will get the exact amount of currency that you had in the block before in the newly forked block. Basically, if the attacker had 20 BTC in block 50, in blue block 51 they would have 400 ETH and in the red block 51 they would still have 20 BTC.
So, post fork, they would still have their 20 BTC and an additional 400 ETH! This is the double spending that happens via forking.
There is another interesting scenario where an attacker may choose to fork. Remember, like we said, under 51% attack most, if not all, the blocks would be mined by the attacker themselves? What will happen, if by some dumb luck, some random miner does manage to create a new block? Well, the attacker will simply fork the chain prior to this new block and continue mining on the new chain anyway!
Now, you may be thinking, what is going to make the rest of the 49% go along in the new chain? The answer to that lies in co-ordination game. Remember, most of the 49% miners will be spread out and independent. They will want to look for their own self-interests. So, in this context we look at game theory, in particular co-ordination game, for answers.
Let’s take an example of the co-ordination game:
Suppose we want to change the language to a symbol based language. Eg:
- Original statement: “Give me your number?”
- New statement: “#?”
If only you speak using this language, it will be a failure because the majority won’t understand what you are talking about and you will be shunned from conversations aka the payoff for you is very low and you have no incentive to change.
However, if the majority of your society shifts to this language and use it exclusively, you will have to change your language otherwise you will never be able to fit in. Now the incentive for you to join is high.
Use the same logic here. The majority of the hash rate is already in the forked chain. You being the independent miner would want to be in the same chain as the majority.
How likely is it that bitcoin could be susceptible to a 51% attack?
Like we have mentioned before, bitcoin did face this scenario once when the Ghash pool exceeded 51%, however the likelihood of that happening is small right now. For an attacker to initiate a 51% attack, the incentives (initially) are very low. The amount of capital required to do a 51% on bitcoin is staggering. Actually, in cases like these, the market price of bitcoin is a great shield. The higher the market price, the more hashing power gets paid for, and the more expensive an attack becomes since resource sourcing gets more expensive.
Now let’s look at more ways that the blockchain could be attacked which have nothing to do with the 51% attack. Remember, most of these examples are purely hypothetical in nature, so don’t go off sounding the alarm bells!
What is “Cannibalizing pools”?
Let’s do a thought experiment.
Suppose, the total hashrate of bitcoin is 100 of which 30 is yours. You effectively have 30% hashrate. Now, suppose the mining reward is 1 BTC, which means, given that you have 30% hash rate you are also expected to get 30% of the mining reward which is: 0.3 BTC.
Now, you have two options:
Option 1: You buy more mining equipment
Suppose you buy mining equipment which increases yours and the network’s hashrate by 1.
Which means, originally we had assumed that the network’s hashrate to be 100 and your hashrate to be 30.
Now the network’s hashrate is 101 and yours 31 which means your own 31/101 *100 = 30.69% of the network hashrate. So that also means that you get 30.69% of the mining reward, which is 0.3069 BTC. So, this means, for every 1% HR that you add to your arsenal, you get a 0.0069 BTC gain (0.3069 – 0.3000).
Option 2: You cannibalize the pool
So, in the previous example, you added 1% hashrate to your own arsenal, what if you were to distribute that hashrate equally among all the miners and you withhold all the valid blocks you mine as well? We will expand on “block withholding” later, but to just give you a brief idea, it basically means that you mine a block but you don’t reveal it to the network and just keep it to yourself.
Let’s look at the mathematics behind it now:
If we take away your 30% hashrate (since you are withholding your blocks, you won’t be getting any rewards via your own hashrates), the rest of the network in total had 70% hashrate.
Which means, normally they get 70% of the block reward which is, in this case, 70% of 1 BTC = 0.7 BTC. But now, since you have distributed that extra 1% hashrate with the rest of the miners, this is how things looks like now:
- Total hashrate excluding your share = 71.
- Honest hashrate = 70.
- Dishonest hashrate = 1.
Since you own 1/71 of all other hashrate, you get:
1/71*0.7 = 0.0098 BTC revenue from the work that other miners have been doing.
Now, let’s compare the two. If you were to do honest mining you get 0.0069 BTC, and if you were to be dishonest then you get 0.0098 BTC. So, it is more profitable to cannibalize pools than to be honest!
What is Block Withholding?
Block withholding is another form of selfish mining. Imagine this scenario, you are a miner in the bitcoin network who uses the most sophisticated and greatest ASICs. Mining blocks is a very easy task for you.
So, suppose you mine a bock, but you don’t reveal it to the network. Instead of announcing to the network and collecting your reward, you keep the block a secret and mine on top of that block. This is what that looks like:
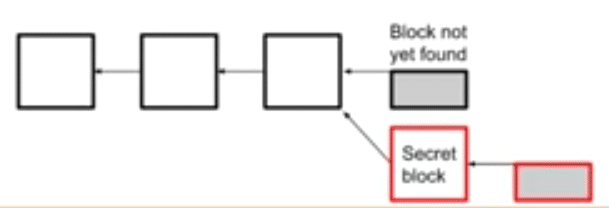
Image courtesy: Blockchain at Berkley
The “secret blocks” are the ones that you have mined and withhold from the rest of the network. When you do find another block, you can reveal the two blocks to the network. What this will do is the following:
- Double the reward that you could have collected.
- Be the block dictators in two blocks instead of one and hence double the amount you can earn via transaction fees.
The reason why it is called “selfish”, is because you are going against the very idea of “equal opportunity for all” that mining stands for. Everyone must have a fair shake at mining and discovering their own blocks. Plus, this can also lead to network monopolization.
Anyway, there are two ways that this can pan out:
Scenario #1: A miner mines a block after you have already mined two blocks
So, what happens if a miner managed to mine a block after you have already mined 2 blocks in secret? You will both broadcast the information to the network. The network will see that you have the longer chain and will give your blocks the nod over the other solitary block. Which means that that block will be orphaned:
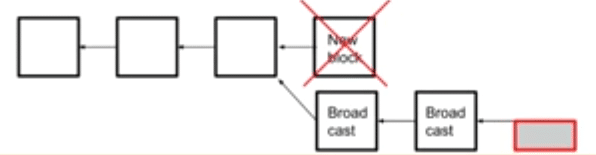
Image courtesy: Blockchain at Berkley
Scenario #2: A miner mines a block before you could mine a second block
What will happen if you weren’t able to mine a second block over your first one and someone was already able to mine a block?
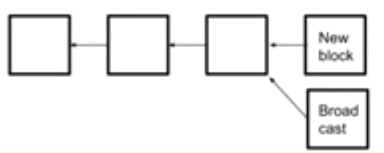
You will both broadcast this to the network and instigate a race for approval.
However, the thing is that you still have 50% probability of getting your block approved which are still good odds to work with.
What is P+Epsilon Attack
A proof of work system is vulnerable to a particular type of attack called the “P+ epsilon attack”. In order to understand how this attack works we must define some terms before hand. Un-Coordinated Choice Model: An uncoordinated choice model is a model where all the participants don’t have the incentive to work with one another. The participants may form groups but at no time is the group big enough to become a majority.
Coordinated choice model: This is a model where all the participants coordinate because of a common incentive.
Now it is assumed that the blockchain is an uncoordinated model, but what if there is an incentive for the miners to do an action which goes against the integrity of the blockchain? What if there is a bribe involved to make the miners take a particular action? This is where the bribing attacker model comes in.
What is the bribing attacker model?
Imagine an uncoordinated model. Now what if an attacker enters the system and incentivizes the miners to coordinate with each other after giving them a bribe? This new model is called a bribing attacker model. In order to successfully bribe the system, the attacker must have two resources:
- Budget: The total amount of money that the attacker has that they are willing to pay to make the miners take a particular action.
- Cost: The price that the miner actually ends up paying.
However, if an attacker does decide to attack the blockchain, we arrive in an interesting conundrum… and this is where the “p + epsilon attack” comes in. For reference check out this table:
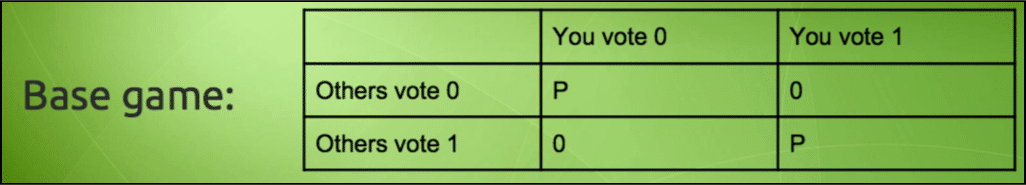
Image courtesy: Vitalik Buterin Presentation.
Imagine a simple scenario such as an election. If the people vote for a particular person if they vote the same way everyone is voting, then they get a payoff but otherwise they don’t. Now imagine, that a briber enters the system and lays down this condition to an individual. If you vote AND the others don’t vote, then you will get a payoff of “P + ε”. The usual payoff AND an extra bribe of ε on top of that.
So now, the payoff matrix looks like this:
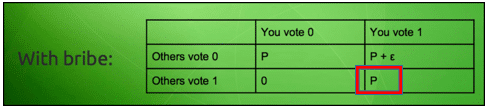
Image courtesy: Vitalik Buterin Presentation.
Now imagine this scenario, everyone involved in this scenario gets to know that if they vote anyway, then there is a chance that they may get a payoff, but if they don’t vote then there is a 50-50 chance of them getting a payoff.
What do you think the players will do then? Of course they are going to vote to get a guaranteed payoff. Now this is where things get interesting. As can be seen in the matrix, the briber only has to pay the bribe “ε” when only person votes while the others don’t. However, in this situation since everyone is voting, the Nash equilibrium shifts to:
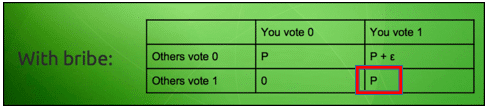
That’s right, the briber didn’t even need to pay the bribe!
So, let’s approach this problem from the POV of the briber:
- Convince the group to vote a particular way.
- Achieve the goal without even having to pay the bribe.
It is a huge win-win scenario for the briber and this has heavy implication on the blockchain especially in a proof-of-work system. Let’s checkout our old hypothetical blockchain again:
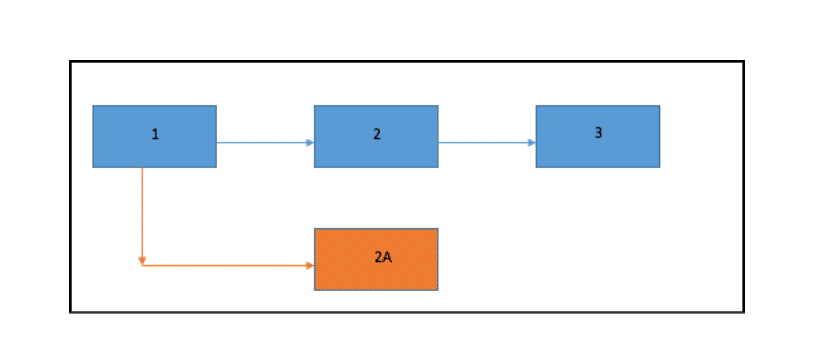
Suppose the briber really wants the chain to hardfork and declares that a group of miner who opts to join the new chain will get a bribe of ε, this will incentivize the entire miner community to coordinate and join the new chain.
Obviously the bribe has to be extremely high for something like this to happen, but as we have seen in the briber attacker model above, the attacker won’t even need to pay the said amount. According to Vitalik Buterin this is one of the biggest problems of the proof of work system, its vulnerability to the P + epsilon attack.
The solution lies in proof of stake.
The solution to this form of incentive driven attack lies in proof of stake. In this system, the miners have to put up a portion of their personal fortune and invest it in future blocks. As an economic system, this is much better because the punishment in it is way more severe. Instead of having their rights taken and getting away with a “tap to their knuckles”, miners now face the very real possibility of their stake and fortune being taken away.
So, how does this help in preventing P + epsilon attacks? Put yourselves in a miner’s shoes. You have a part of your fortune invested inside a block which is to be added in the main chain. Now a briber comes and tells you that you can get an extra payoff if you make your block join the main chain. BUT, if the chain doesn’t get approved then there is a huge risk of you losing all the money that you have invested in the block. Plus, as the P + Epsilon attack states, you won’t even get the extra payoff from the bribe. For a miner, once that they have invested a stake, it is a no brainer for them to continue in the main chain and not to get involved in any malicious activities.
What is a blacklisting?
Blacklisting is a form of attack against a single entity. Imagine that there is a very prominent entity who has a lot of capital and they have it out for this guy named Jake and they want to blacklist them from the network. In fact, let’s assume that this entity is a country who has a lot of pools in their control, let’s called this country Aliceland.
Before we continue let’s create a legend:
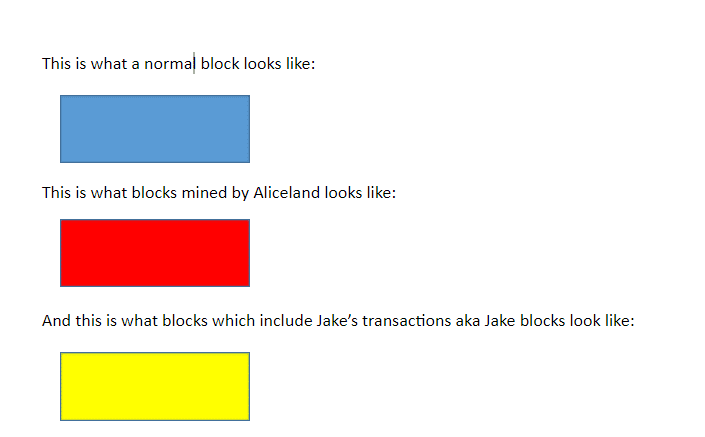
This is what a normal block looks like:
This is what blocks mined by Aliceland looks like:
And this is what blocks which include Jake’s transactions aka Jake blocks look like:
Ok, so there are two ways that Aliceland can blacklist Jake:
- Punitive forking.
- Feather forking.
Case #1: Punitive Forking
There are two different strategies that you can execute via punitive forking.
Strategy 1:
Since Aliceland is a country, it can simply order all of its pools to not include any transactions by Jake in their blocks. Now this is a naive strategy because for it to work there are a lot of things that they will need to consider.
Firstly, they will need to be in control of the 100% of the pools in their country. If even one pool is outside their control, then they may include Jake’s transaction in their block. The maximum that they can achieve by doing this is cause loads of delays and inconveniences.
Strategy 2:
Now what if, Aliceland wants to do punitive forking AND owns >51% of the world’s mining power? This is when the equation completely flips on its head. This is what they will have to do.
Firstly, they will announce to the world that they won’t be allowing any transaction which include Jake in the blockchain anymore and that not a single one of their pools will work on a chain which has a “Jake Block” in it. In other words, the moment a Jake block appears, Aliceland will initiate a fork.
Suppose this is what the blockchain looks like:
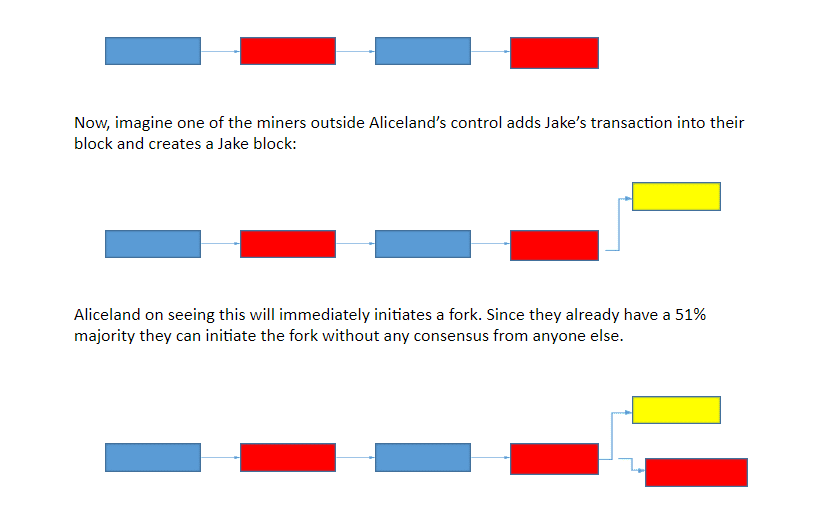
Now, imagine one of the miners outside Aliceland’s control adds Jake’s transaction into their block and creates a Jake block:
Aliceland on seeing this will immediately initiates a fork. Since they already have a 51% majority they can initiate the fork without any consensus from anyone else.
Since they have already announced their intentions beforehand and because they own the 51% majority, no one will dare to go against them and even if they do rebel and include a Jake block, they will be forced to orphan it because Aliceland can simply use their majority to fork and continue.
Case #2: Feather Forking
So, we have seen above how anyone with a 51% majority can backlist anyone using punitive forking. Now, what can you do if you want to blacklist someone but you don’t own a 51% majority? Aliceland can actually still blacklist poor old Jake by a method called feather forking. Let’s see what that means.
Aliceland can declare that whenever a Jake block is added, they will attempt to fork, but give up after a certain number of confirmations (Confirmations = the number of blocks mined on top of the contested block). This is different from punitive forking in the sense that Aliceland is not threatening a permanent fork, they are instead saying that they will fork every time BUT will also come back after a certain number of confirmations.
Let’s see an example:
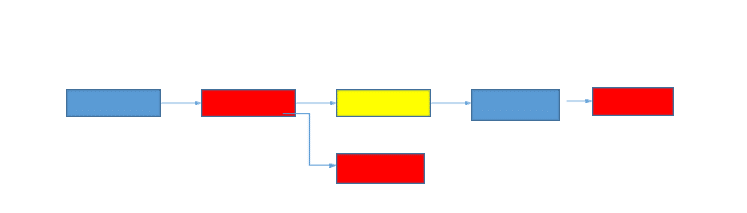
So what happened here?
When the Jake block got added to the system, Aliceland did a fork and waited for a confirmation. In this case, the confirmation was 1 block. The moment that block got appended to the Jake block, Aliceland vacated the fork and joined the main chain again.
Now you might be thinking, “That’s not that bad.” But let’s look into the mathematics of the whole thing.
Suppose Aliceland has “q” hashing power where 0<q<1.
Then, going by Bernoulli’s distribution, the chance of mining a block and forking is q^2.
Going by our example, we will assume that Aliceland is waiting for only 1 confirmation.
Suppose, Aliceland has 20% of the world’s hashing power, so q = 0.2 and the chance of mining a block is 0.2^2 = 0.04 = 4%.
4% chance may not seem that high, but the other miners are now aware that there is a 4% chance of their blocks getting orphaned IF they do include Jake blocks.
So, what is the expected value (EV) that the miners can get IF they include/don’t include Jake blocks?
- EV (including Jake block) = (1-q^2)*block reward + Jake transaction fees.
- EV(not including Jake block) = Block Reward.
So, for the miners to get equal EV from both the scenarios, Jake will have to pay transaction fees which are equivalent to q^2*block reward. Let’s see how much that is in context of bitcoin.
Block reward = 12.5 btc and in this example q^2 = .04.
Substituting the values in this equation:
- q^2*block reward
- And we get: .04*12.5 = 0.5 BTC.
- 0.5 BTC,as of writing, is equal to $2091.
That’s how much Jake will have to pay in transaction fees EVERY single time to make it worthwhile for the miners to put in a Jake block to the main chain. Not the most convenient of scenarios to say the least!
What is transaction malleability?
Let’s start off with a brief overview of what a hashing function does. A hashing function can take in any input of any length but the output it gives is always of a fixed length.
However, there is one another important function of hashing that you need to know to understand the “transaction malleability bug” as it is called. Any small change in the input data will drastically change the output hash.
Eg. Checkout this test that we did with SHA-256 aka the hashing algorithm used in bitcoin:

We just changed “T” from uppercase to lowercase, and look at what it did to the output!
One more thing that you need to understand about the blockchain is that it is immutable, meaning, once the data has been inserted in a block, it can never ever be changed. While this proves a safety net against corruption, there was one weakness that nobody saw coming.
What if, the data was tampered with before it even entered the block? Even if people found out about it later on, there was nothing that anyone can do about it because data once entered in a block can never be taken out! That in essence is why malleability of transactions is such a problem.
Now, why does transaction malleability happen?
Turns out that the signature that goes along with the input data can be manipulated, which in turn can change the transaction ID. In fact, it can make it seem like the transaction didn’t even happen in the first place. Eg. Suppose you have a set of blocks which says “3+1 = 4” and then someone comes along and changes that to “2+2 = 4”, the outcome is still the same in both the cases “4”, but the inner transaction details have all been greatly muddied as a result.
Let’s see this in a blockchain related example.
Suppose Bob wants Alice to send him 3 BTC. Alice initiates a 3 BTC transaction to Bob’s public address and then sends it over to the miners for approval. While the transaction is waiting in the queue, Bob uses transaction malleability to alter Alice’s signature and change the transaction ID.
Now there is a chance that this tampered transaction will be approved before Alice’s gets approved, which in turn overwrites Alice’s transaction. When Bob gets his 3 BTC, he can simply tell Alice that he didn’t get the 3 BTC that she owed him. Alice will then see that her transaction didn’t go through and will them resend it. As a result, Bob will end up with 6 BTC instead of 3 BTC.
One of the most famous example of the transaction malleability attack was the 2014 Mt Gox attack. Mt. Gox was one of the biggest bitcoin exchanges in the world and around $450 million worth of bitcoins were stolen from it.
Now that bitcoin core has initiated Segwit, it is going to stop transaction malleability in BTC.
What is timejacking?
The last possible attack that we want to talk about is “timejacking”. The bitcoin system uses a network of nodes to relay messages and information. Every node needs to keep track of time AND it needs to be in synch with its other peer nodes. The way it does that is by keeping an internal clock system which happens to be same as the computed median clock time of all its peers. If this median time differs by more than 70 mins from its system time, then the internal clock readjusts and reverts to the system time.
So, as a precaution, and this is very important to understand wrt the attack, the nodes reject any block that are more than 120 mins ahead of its internal clock. Now suppose there is an attacker who wants to attack a particular target node. How will they go about it?
- First, they launch a Sybill attack on the bitcoin network. A Sybill attack is an attack where an attacker has control over multiple nodes in the network, this can happen by spawning thousands of bogus nodes and attaching them to the network.By doing the attack, the attacker manipulates the time stamps of the nodes in such a way that the target node is 70 mins behind the clock while every other node is 70 mins ahead (Why 70? So that it is still under the 70 min limit and that the clock doesn’t revert). This basically creates a 140 mins gap between the target node and the rest of the network.
- Now, the attacker, using their hashrate power mines a new block with a time stamp that is 190 mins ahead of the real time.
- When this new block is broadcasted, the target node immediately rejects it since, according to them, it is not within the 120 min limit. For the target node, the block is (190+70), 260 mins behind.
- However, every other node accepts the block because it is within the 120 mins limit (190-70 = 120) and the miners in all these other nodes start mining on it.
- So, the attacker has now successfully partitioned the target node from the rest of the network. The target node starts working on their own chain while everybody else is working on theirs.
- The attacker can now mine out more free blocks from the target node and engage in double spending. In fact, if they keep adjusting the timejack, they can keep it going indefinitely.
Timejacking is a very scary propositions. In fact, a group of a malicious miners can timejack a group of miners and take them out of the system and increase their hashrate percentage in the process.
Hypothetical Attacks on Cryptocurrencies Conclusion
So, that’s a list of possible attacks that can happen to cryptocurrencies. Keep in mind, these attacks, or at least most of them, are purely hypothetical in nature. The idea is to not increase paranoia; the idea is to educate everyone about cryptocurrency and the technology behind it. If you can think of a possible hypothetical attack that we haven’t mentioned yet, then do comment below and let us and everyone know.




















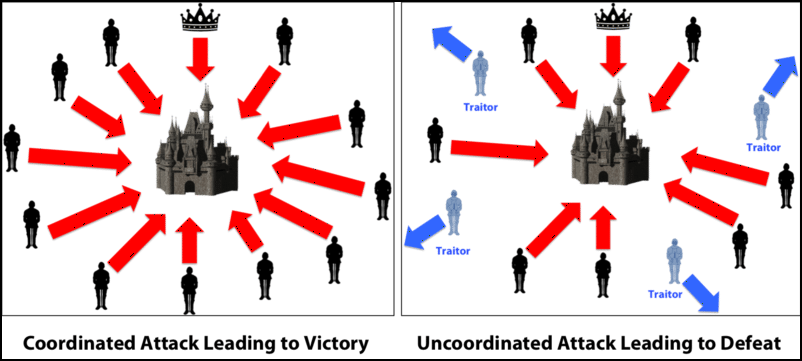
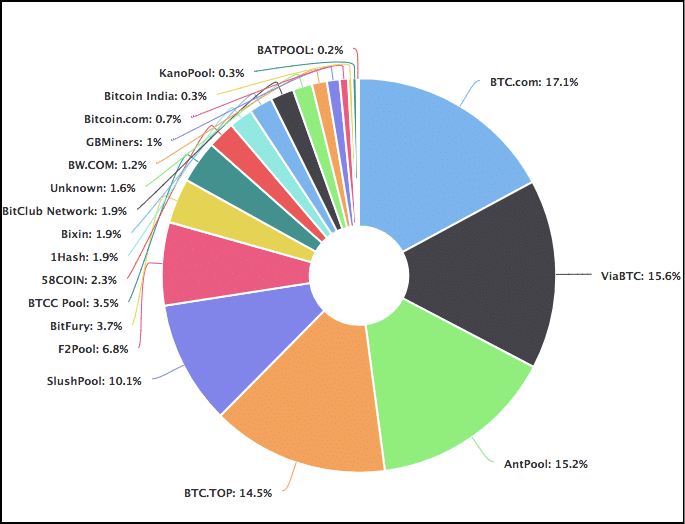 Image Credit: Blockchain.info
Image Credit: Blockchain.info
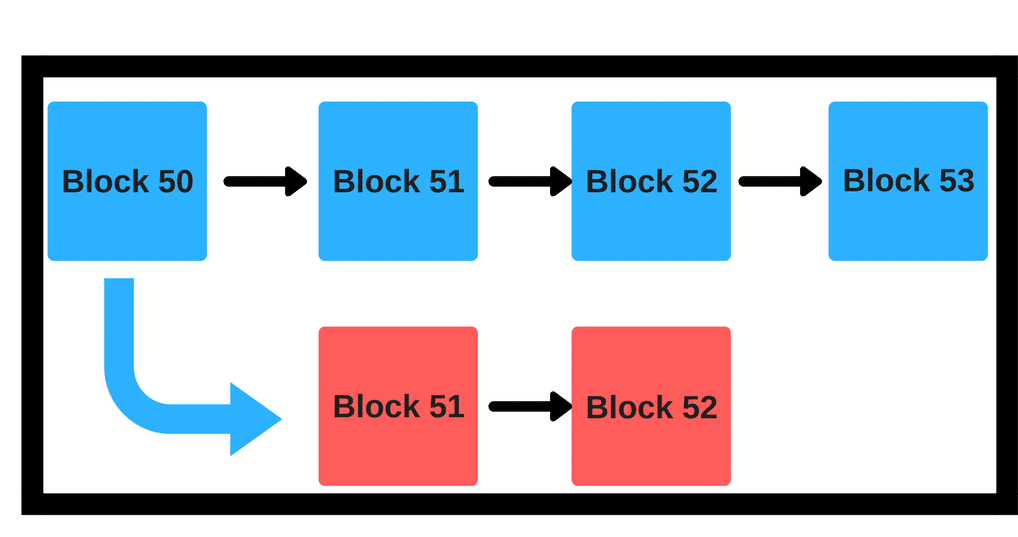
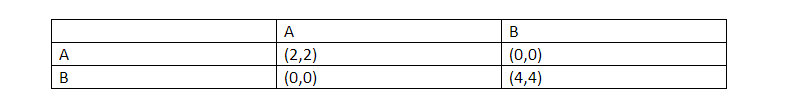
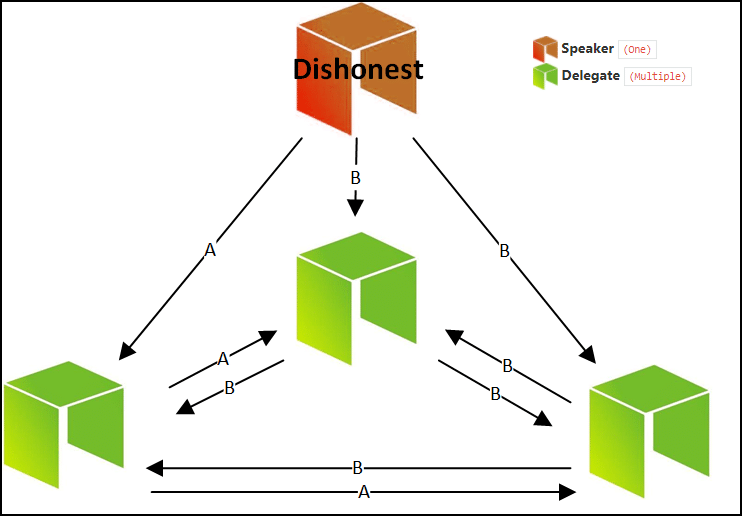
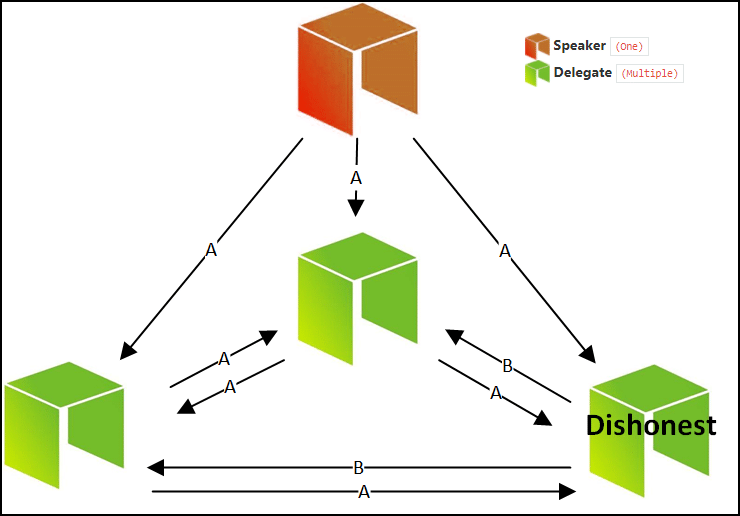

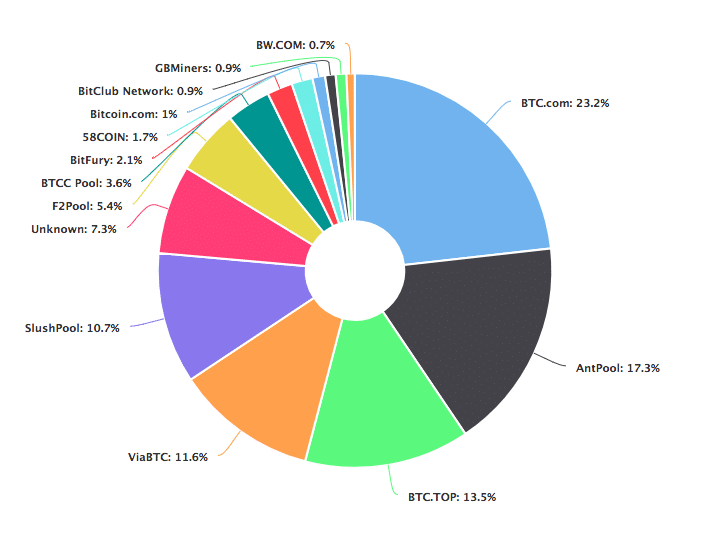 Image Credit: Blockchain.info
Image Credit: Blockchain.info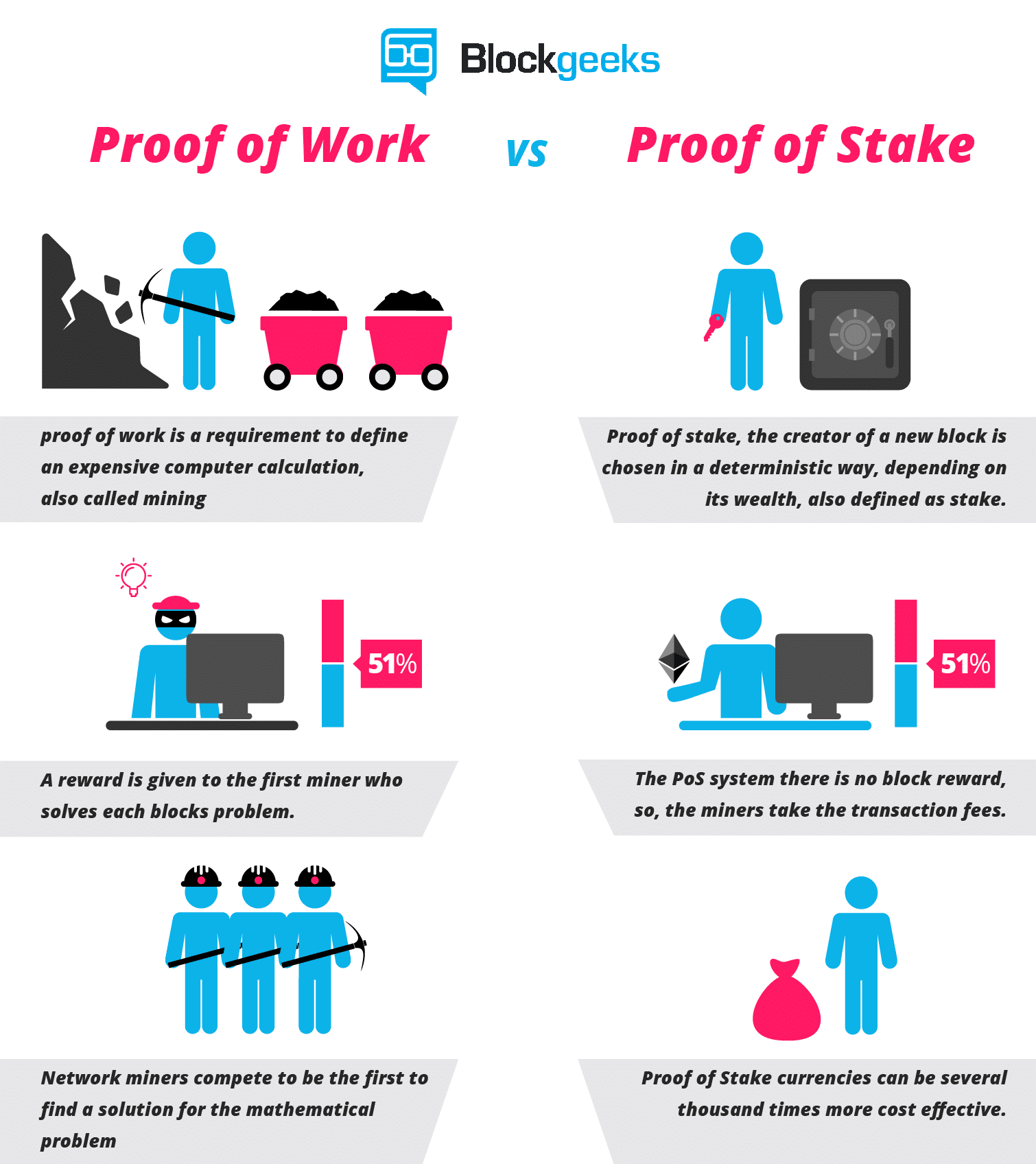
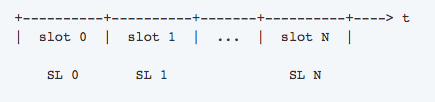
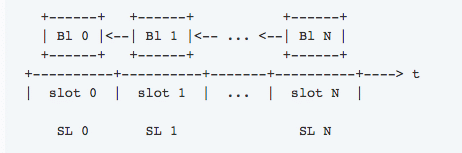





 Image courtesy: Blockchain.info~50% of the world’s bitcoin supply is being mined by 4 pools!! Just 4!Bitcoin is supposed to be a decentralized currency, but how decentralized can it really be if nearly half of it is controlled by 4 pools?Unfortunately, this is not a problem exclusive to Bitcoin, checkout the hashrate distribution chart of
Image courtesy: Blockchain.info~50% of the world’s bitcoin supply is being mined by 4 pools!! Just 4!Bitcoin is supposed to be a decentralized currency, but how decentralized can it really be if nearly half of it is controlled by 4 pools?Unfortunately, this is not a problem exclusive to Bitcoin, checkout the hashrate distribution chart of 











